CCleaning Up The Trojan Mess

 I came across an article a couple of days ago that explained how hackers had managed to embed a “decapitated botnet” (trojan malware) into the installer package of the computer storage and registry utility CCleaner (version 5.33, released August 15, 2017), by Piriform Ltd., which was recently purchased by security giant Avast.
I came across an article a couple of days ago that explained how hackers had managed to embed a “decapitated botnet” (trojan malware) into the installer package of the computer storage and registry utility CCleaner (version 5.33, released August 15, 2017), by Piriform Ltd., which was recently purchased by security giant Avast.
As reported:
Talos recently observed a case where the download servers used by [the] software vendor to distribute a legitimate software package were leveraged to deliver malware to unsuspecting victims. For a period of time, the legitimate signed version of CCleaner 5.33 being distributed by Avast also contained a multi-stage malware payload that rode on top of the installation of CCleaner.
Yes, you read that right: Avast, makers of renowned security products Avast Antivirus Pro Plus and Avast Internet Security, has been inadvertently distributing trojan malware in the installer package of an immensely popular tool that many IT professionals use regularly to eradicate the remnants of other viruses and, err–malware–from infected PCs. I can hear them all now, in collective, confused unison, reciting the tired old refrain:
“Well, that didn’t work.”
So, this got me wondering: is there a product on the market that would allow an IT manager in an academic, corporate, or government institution–charged with maintaining thousands of PCs–to determine which computers on his or her network had this version of CCleaner installed, even if antivirus software was not yet aware of the threat? Could this product show which computers were actively using the infected product at that very moment, and give him or her the power to immediately block not just future installations, but actually prevent, in realtime, any further launches of the product or its installer on network connected machines?
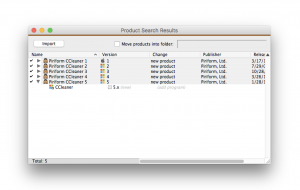
Okay, yes, I embedded a couple of trojan rhetorical questions here. After learning about the threat, the first thing I did was to look up CCleaner in our proprietary Product Recognition Service (PRS) to find the rogue revision. There it was. Luckily, CCleaner had not been installed recently on any of our machines.
If a company that makes one of the largest and most advanced antivirus software packages on the planet can be tricked into infecting its own clients’ computers with trojan malware, then it’s safe to say that anything can happen. Faced with a threat like this, why should you be forced to wait for Avast or McAfee to update their antivirus definitions and push out an update, just so you can blindly deploy “fixes” without ever really knowing the extent of the damage? K2 could have told you exactly which computers had CCleaner 5.33 installed, allowing you to immediately isolate the affected machines, while also blocking the launch of the infected products on every other computer on your network (with the KeyAccess client installed).
Let’s be clear: K2 is not a computer or network security tool, and I’m not suggesting that you use it to discover or remove viruses from your network. The point is, K2 isn’t just a “license manager,” either. Examples like this make me think of it more as a “Software Operations Command Center,” giving IT administrators deep, realtime intelligence and control over the state of their entire computer network; not necessarily at the hardware level, but at the level of installed and active software. It’s just another way K2 works for you.
Author: Jason Schackai
Training and implementation specialist by day, user experience designer by night, Jason helps users learn the ropes of Sassafras, while mining their difficulties for ways to improve the product. As his father once told him: “Join me, and I will complete your training. With our combined strength, we can end this destructive conflict and bring order to the galaxy!”
Site Search
Documentation Search
Categories

Social
Subscribe
| Thank you for Signing Up |