Any organization using KeyServer has a powerful tool for learning how and where computers and software are being used. Using KeyServer, policies can be configured which specify how product usage […]
Currently browsing: Tech Blog
Lab Computer and Software Availability Maps in K2 KeyServer
Though availability maps have been around since the 7.2 version of KeyServer, we’ve found that many K2 administrators either still aren’t aware of them, or they just aren’t sure where to start […]
Active License Management with KeyServer
Sassafras supplies an API that third party vendors use to build KeyServer support directly into their products. A vendor builds a custom license (.lic) file that includes basic details (such […]
K2 KeyServer After High Sierra (64 Bit Compatibility)
Last year Apple announced that High Siera (10.13) would be the last version of OS X to support 32 bit applications. Furthermore, starting in 2018, beta versions of the current […]
Hardware Guidelines for the KeyServer Host
We are often asked by new K2 administrators for our recommendations on the system that will host their KeyServer. While there is no optimal system configuration — each KeyServer has different usage patterns and […]
Cost Savings Using the Product Optimizations Report
One of the reports we have recently added is the Product Optimizations report. This report aims to help you achieve cost savings by pointing out alternatives to expensive suite products. […]
Importing Data to Computer Asset Fields
K2 is a powerful Hardware Asset Management tool. The KeyAccess client collects many hardware properties which are saved in the Computer Database. However, Computer records also have some additional fields […]
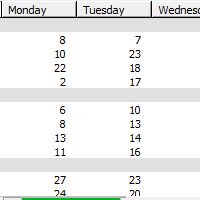
New Login Reports
In the 2015-02-25 image, we have added six new Login reports. Here’s a quick peek at one of them: The report above lets you easily compare computer utilization on different […]
Taming Bentley SELECT Licensing to Reduce Costs with Sassafras K2
Bentley SELECT software licensing can be closely managed by Sassafras K2 to avoid excess usage charges in Bentley’s quarterly billing statements. A K2 policy configured to track and manage licensing […]
Integrating Active Directory with K2
K2 has supported integration with Active Directory authentication for many years. Since AD and K2 deal with computers and users, it is natural to leverage existing configuration, avoid duplicated efforts, […]
Site Search
Documentation Search
Categories

Social
Subscribe
| Thank you for Signing Up |