Choosing a Computer ID Type

With any system that maintains a database of computers, a critical question is how each record is uniquely identified. For many organizations, identifying computers simply by Computer Name is sufficient – but there can be reasons to consider other data points. In particular, if computer names are not well regulated, it is safer to create a one to one association with physical hardware, by using the MAC address of each computer.
Computer IDs in KeyServer
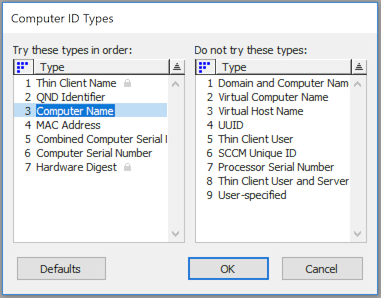
KeyServer defaults to using MAC address, since using Computer Name can have potentially significant downsides. However, you might want to change this configuration when you first install KeyServer. If you know that your computers names will be unique, and will not see frequent changes, then you should use the “Computer ID Types” dialog to move “Computer Name” above “MAC address” as shown below.
In short here are a few quick things to know about Computer IDs – which you can read about in more detail further on in this post:
- Use Computer Name if you want usage reporting to tie to the computer name, even across a hardware replacement
- If you are setting up Lab Availability Maps, using name as the id avoids having to reconfigure maps when hardware within the lab is replaced
- If computer names are not unique, MAC address is a better ID type, to avoid having multiple pieces of hardware “sharing” a record
- Some computers can be forced to use a different id than the global setting, using registry entries (contact Support)
- Virtual Host Name might be useful for virtual machines (especially dumb clients)
A longer description of each ID type is available in the Computer ID Types Documentation – note however that usually when you’re making changes to this configuration, you should do so with the help of Sassafras tech support. It is also possible to choose one default for all computers, but then force certain subsets to use a different ID type.

Two conceptual choices
At a conceptual level, there are two main ways to handle unique identification of computers. First, they can be treated as physical entities – so the goal is to have exactly one record for each physical piece of hardware (ignoring Virtual Machines briefly, which of course can also be tracked). Alternatively, they can treated as functional or logical entities – which is to say that a single record ties to data for an older piece of hardware as well as a newer piece of hardware that replaces it.
More specifically, our default ID type will use the MAC address of each computer to identify it. This is meant to tie strictly to the piece of hardware. The most obvious alternative is to instead form a Computer ID using the Name of each computer so that a given computer record is more of a functional object. In a static environment where nothing ever changes, this choice would be fairly unimportant. The choice becomes important to understand any time a computer can be renamed, or replaced by a new piece of hardware.
Essentially it comes down to the question of old usage – should it be reported as occurring on the physical hardware (even if that hardware now has a very different name and “lives” elsewhere) – or should it be reported as occurring on the same computer name (even if that name is now associated with entirely different hardware). Let’s take a look at some examples to better understand the implications.
MAC Address based IDs
First, suppose you want a single record for each physical piece of hardware. If the name of the computer gets changed, you simply want the existing record to get updated with the new name. Also any usage generated from this piece of hardware, regardless of the name at the time, should all be grouped together in reports. To achieve this behavior, use our default Computer ID types, where MAC address will be used. Let’s follow a simple scenario.
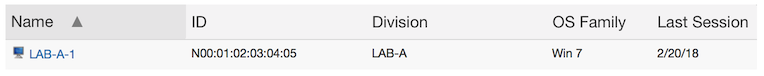
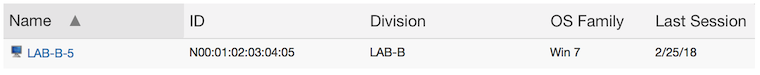
We start out with a single computer. It is discovered by KeyServer and a single record exists. Suppose that a single login occurs with a duration of 5 hours.
Next that same computer is renamed as it gets moved into a different lab. Because the id is tied to the hardware, KeyServer continues to have only a single computer record. The name is updated to reflect the new name. Someone logs in to the computer in LAB-B for 3 hours.
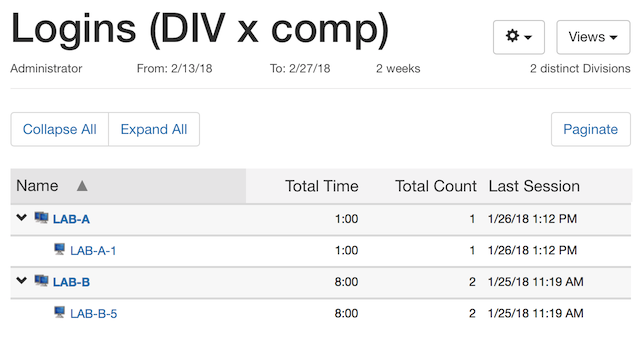
Now in the first lab, a new computer is purchased. It gets discovered by KeyServer and creates a second record, since it has a different MAC address. Note that we’re upgrading LAB-A – the old computer had Windows 7 installed, the new one has Windows 10. This new computer has a login of 1 hour.
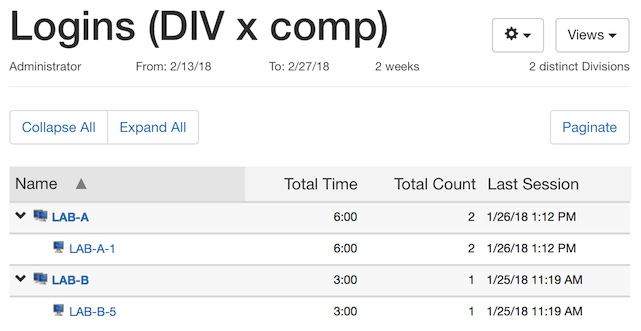
Now we run a Logins report. Notice that the first two logins (for 5 hours and 3 hours) both are summarized under “LAB-B-5” since both occurred on the hardware that is now named LAB-B-5. Since that computer record is now associated with the LAB-B division, all usage appears within that division.
This aspect of where usage is reported is one reason that you might want to use the Computer Name as the ID, instead. Even though the first login used the hardware that is now in LAB-B, it happened while that hardware was in LAB-A.
Name based IDs
If you want to treat computers more functionally – i.e. there’s always going to be a LAB-A-1 computer, regardless of the hardware it runs on – then you likely want to use Computer Name as the primary ID. Let’s take a look
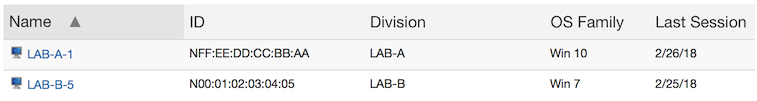
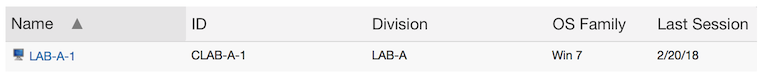
As before, we start off with a single record in KeyServer, after the initial 5 hour login.
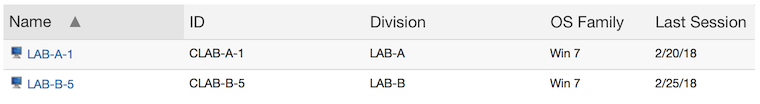
This time, however, we get a second computer record as soon as the computer gets renamed. Even though so far only one piece of hardware exists, KeyServer has separate records for when that hardware was named LAB-A-1 vs LAB-B-5. Both records show Windows 7 as the OS, since that’s the only OS that has been used when logging in.
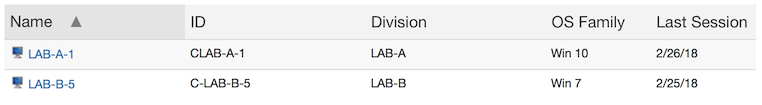
Now new hardware is installed in LAB-A. Because the name of the new computer is the same as the old name of the original hardware, it connects to the existing (original) record. At that point any relevant properties are updated – in this case LAB-A-1 now shows that it has Windows 10.
Under this configuration, running the Logins report shows each login summarized under the name of the computer when the login occurred. So LAB-A-1 shows the first 5 hour login on the old hardware, in addition to the third 1 hour login. LAB-B-5 shows the second login which lasted for 3 hours.
Summary
Computer IDs can be a complicated topic. KeyServer has a lot of flexibility for how it identifies computers, and there are a lot of different variations that can come up in your live environment. We’ve described the most common cases above, but feel free to contact us to discuss or ask questions about your own environment.
Author: Michael Maddalena
Having tested and supported KeyServer since as far back as version 3.2, Michael has been working with some long-term customers for decades now, but is always happy to help anyone (Old Hands, New or Recent customers, or Prospects) understand and get the most out of our software. He also handles any questions related to bees or goats.
Site Search
Documentation Search
Categories

Social
Subscribe
| Thank you for Signing Up |