Create Shadow Certificate
 Note that the use of Shadows is considered a legacy mechanism is and rarely used anymore. Robust virtual server hosting has made this redundant server setup antiquated. Additionally, it's important to note all data during a Shadow event is not reported to the main server, but cached data on a client due to short outage is.
Note that the use of Shadows is considered a legacy mechanism is and rarely used anymore. Robust virtual server hosting has made this redundant server setup antiquated. Additionally, it's important to note all data during a Shadow event is not reported to the main server, but cached data on a client due to short outage is.
The KeyServer installer is also used when creating KeyShadows - but these installations must use copies of a "shadow.lic" license certificate. This has been created within KeyConfigure while connected to the main KeyServer, instead of the "server.lic" which is used only on the KeyServer host.
Server Host
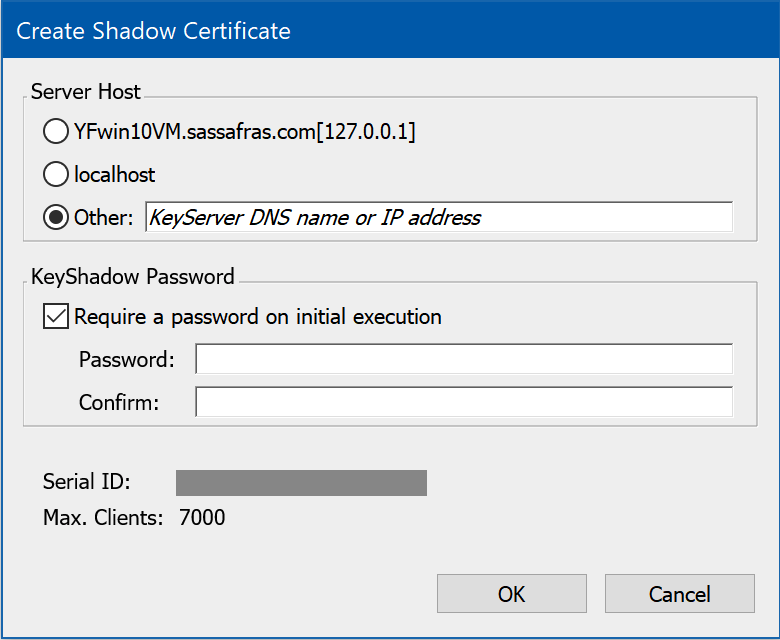
To create a shadow.lic, select "Create Shadow Certificate" from the Config Menu. The configuration dialog offers three ways to enter an address for the KeyServer. For most purposes, it is best to enter the same DNS value that you have specified in the KeyAccess client configuration. Whenever a client connects to a KeyShadow for any reason, the client will adopt the KeyServer address from the shadow.lic and use it to replace the "KeyServer Address:" value specified in the KeyAccess logon configuration. Keeping these address specification exactly the same will avoid surprises in the future.
Depending on how your DNS server is configured, the "address" might be the DNS name for the KeyServer host computer itself or perhaps a DNS alias for the KeyServer service. Using a cname is often the most flexible option if you ever need to migrate the KeyServer in the future. Using a fixed IP is allowed, but not recommended as it's not as flexible. You would need to ensure the IP moves to the new server in such a migration event.

![]() Years ago, when DNS servers were less reliable, it was common to configure the shadow.lic with the actual ip address of the KeyServer host or a combination of the host name and ip address. These options are still available as radio buttons, but now they are rarely needed. And, whenever a client has gotten service from a KeyShadow, using these radio button options will cause any DNS value, formerly specified as the KeyAccess logon address, to be overwritten with an ip address. Then if you ever need to direct clients to a new KeyServer host address in the future, it will no longer be a simple matter of re-configuring your DNS server with a new ip resolution for the KeyServer name.
Years ago, when DNS servers were less reliable, it was common to configure the shadow.lic with the actual ip address of the KeyServer host or a combination of the host name and ip address. These options are still available as radio buttons, but now they are rarely needed. And, whenever a client has gotten service from a KeyShadow, using these radio button options will cause any DNS value, formerly specified as the KeyAccess logon address, to be overwritten with an ip address. Then if you ever need to direct clients to a new KeyServer host address in the future, it will no longer be a simple matter of re-configuring your DNS server with a new ip resolution for the KeyServer name.
KeyShadow Password
In order to prevent duplicated copies of the KeyShadow software from running on unauthorized computers, the shadow installation can be protected by a "shadow password" which must be entered when the KeyShadow process is launched for the first time on a new host computer (as explained in the KeyShadow installation instructions). You have the option of specifying this password or creating a certificate that does not require a password. Once a shadow has successfully connected to the KeyServer, it will appear in the Shadows window where its status is shown.